Cyber Sphere’s patented technology can solve a wide range of problems for small businesses, large companies, government organizations, individuals, and more. Everyone deserves to be secure.
Critical Unclassified Information (CUI) Management
The U.S. Government is requiring DoD contractors to implement processes and tools for Controlled Unclassified Information (CUI, see https://www.dodcui.mil/). NIST 800-171 and emerging CMMC 2.0 requirements dictate how contractors and sub-contractors manage CUI. Cyber Sphere and our core technology are ideally suited to address these challenges. We can provide client-side app or web interfaces in Chrome, Safari, iPhone, Android, etc. to enable U.S. DoD and Industry organization compliance. We can provide an SDK for integration with existing platforms such as Salesforce and Oracle. Cyber Sphere’s team has decades of experience with DoD contractor information security requirements.
Cyber Sphere’s rFiler encryption tool is an easy-to-use CUI management tool:
- Most networks and servers do not offer discrete file access control due to cost impacts and implementation difficulty
- DoD contractors handling sensitive unclassified DoD information will be required by DFARS to achieve a particular CMMC level as a condition of contract award
- Controlled Unclassified Information (CUI) is the most challenging aspect of CMMC; CUI transmission requires encryption. All but the largest DoD contractors face severe financial and manpower constraints
- OLE-based CUI management system – simplifies and reduces cost of compliance for CMMC 2.0, reducing the impact of compliance on DoD contractors and subcontractors
- Organizations can pre-define groups, e.g. engineering, program management, finance, etc.
- The system facilitates easy encryption of data for storage and transport and has a built-in email client
- Object-Level Encryption (OLE), each file or folder has an individual access control list designated by the file or folder originator
- Cyber Sphere conforms with the 17 practices for CMMC V2 Level 1
- Product roadmap includes compliance with 140 practices for CMMC V2 Level 2
- Provides defense in depth to applicable CMMC V2 Level 1 and Level 2 practices
Classified Data Management
Cyber Sphere’s OLE (Object-Level Encryption) applies access control lists to individual files and folders. Systems can be shared and maintained while files remain secured. OLE facilitates precise need-to-know control of each file. The file originator can redact any file or message and set document time limits for use.
Real-life needs for our technology:
In 2023, an Air Force reservist posted dozens of secret intelligence reports and other sensitive documents on a social media server. Air Force officials caught Airman Teixeira taking notes and conducting deep-dive searches for classified material. With Cyber Sphere’s OLE Access Control Lists, Airman Teixera would have been denied access from ever even seeing this material.

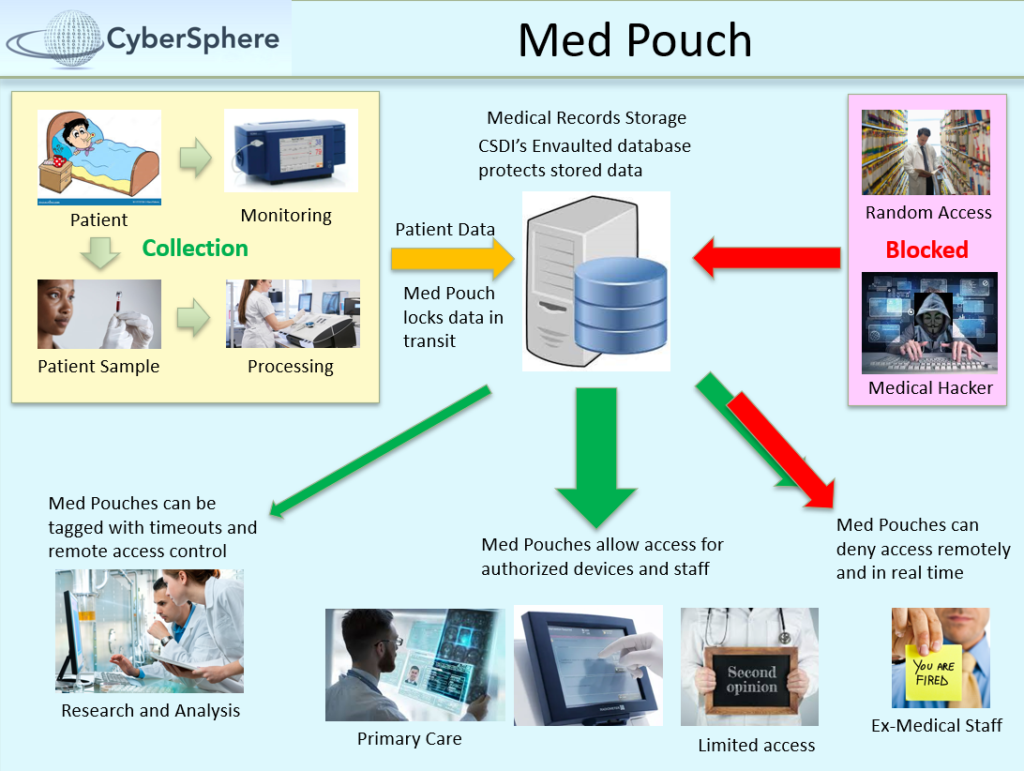
Personal Healthcare Information Management – MedPouch
Cyber Sphere’s existing technology can provide a secure solution to patient data storage and transfer. This healthcare-based spin on the rFiler will contain pouches of medical data known as MedPouches. This approach will provide the same high security and peace of mind as the rFiler while complying to PII and HIPAA.
Secure Machine Communication
Water/wastewater and distributed energy utilities need secure machine communications, but small and medium utilities lack the funding and IT expertise to implement and operate secure infrastructure. This is where Cyber Sphere’s patented technology comes in. Our OLE (Object-Level Encryption) technique can be used to apply message-level encryption that protects data and commands even if the network boundary is breached. The control systems can be programmed to detect and disregard any unauthorized commands and unauthorized detection can trigger automated response and reporting.
