Our Approach
Object Level Encryption (OLE)
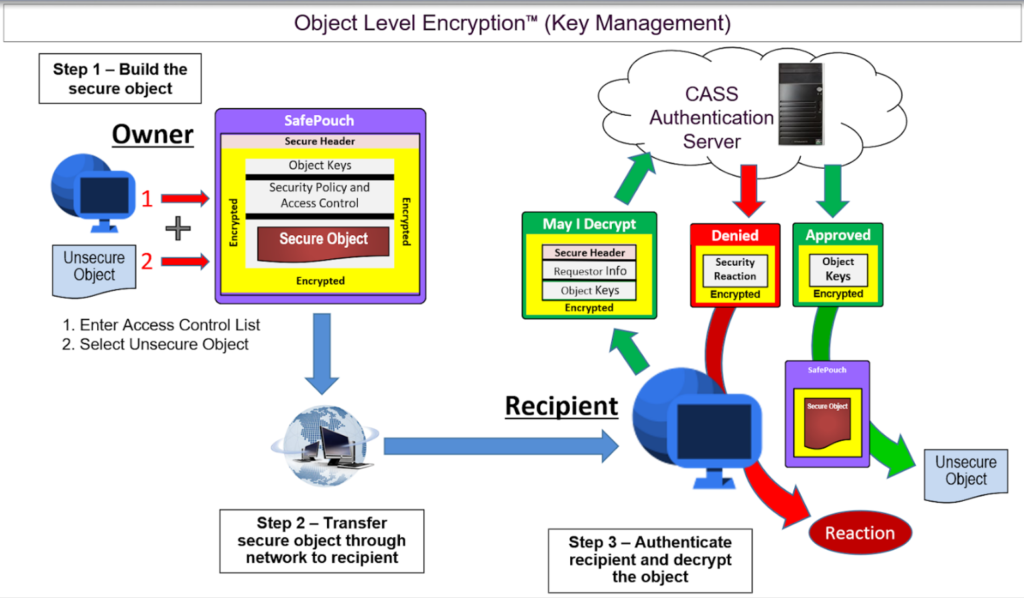
Cyber Sphere’s technology is rooted in Object Level Encryption. In our applications, this encryption as well as the key management is fully automated and applies tailored protection to each file or group of files. Users define ad-hoc group or individual Access Control Lists (ACL) for each file or folder for flexible workgroup definition based on need-to-know and these files are protected even if network or server intrusion occurs. There are no file size limits. Objects are encrypted on the originating computer, not a central server or cloud. Encrypted objects can be safely stored and moved, even outside the network, and are only accessible by pre-authorized individuals. It also detects and reports unauthorized access attempts and can be scripted to trigger an automated response. There can be revocation based on ACL changes, time limit, etc.
Work Groups and Access Control Lists (ACLs)
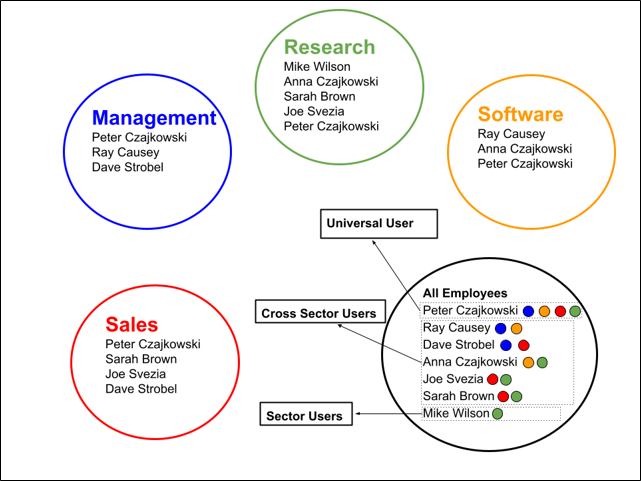
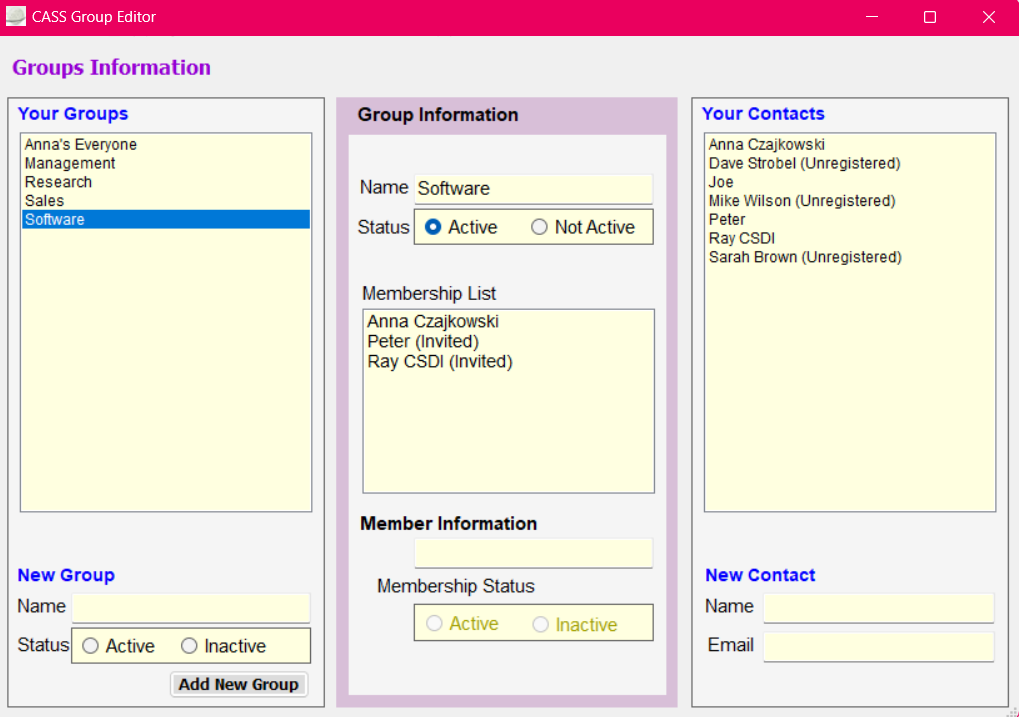
Users can be organized into work groups. Files sent within these groups can only be received and devaulted by users within that group. Universal users are members of all work groups within an organization, cross sector users belong to more than one work group but not all, and sector users belong to just one.
Customer Authentication Security Server (CASS)
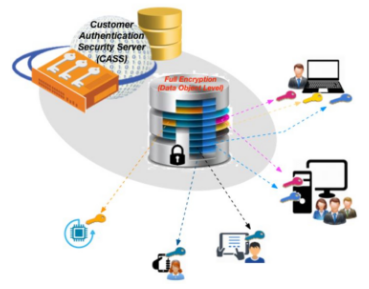
Cyber Sphere’s product suite is built around the CASS, which integrates into the clients’ IT system and scales to meet the specific needs and requirements of each client. The CASS implements Cyber Sphere’s core technology, AutoSafe, which is a patented encryption key management protocol, along with a powerfully customizable user/group profile system. The result is a secure, scalable, and transparent system that can be implemented either inside the client’s firewall or in the cloud.
Object Level Firewall (OLFW)
Our encryption key management method and protocol can protect “data at rest” and “data in motion”. This technology was developed to meet the needs of U.S. Government data security applications. This system not only protects the data but can detect and react to attempted intrusions. Cyber Sphere’s products can be used in a wide range of government and commercial computer and network applications.
Robust Access Management
Managing access to encrypted data is a hassle without transformative technology. Deciding to use encryption techniques such as PKI certificates is expensive, labor-intensive, and overly complicated. With all of the hurdles preventing people from protecting their data, it makes it difficult to achieve security. With Cyber Sphere’s system, managing access is simple, transparent, and cost effective. Access to specific data can be based on user, device, location, time, and a variety of other parameters, giving the client complete control of their data. Better yet, data does not have to be re-encrypted every time its access settings are changed, saving time and resources.
Patents
Object Level Encryption (OLE) System/ Encryption Key Management System
U.S. patent no. 9,485,229: Read more about this patent here.
Key Management Method Protecting an Object Level Database
U.S. patent no. 10,909,254: Read more about this patent here
rFiler
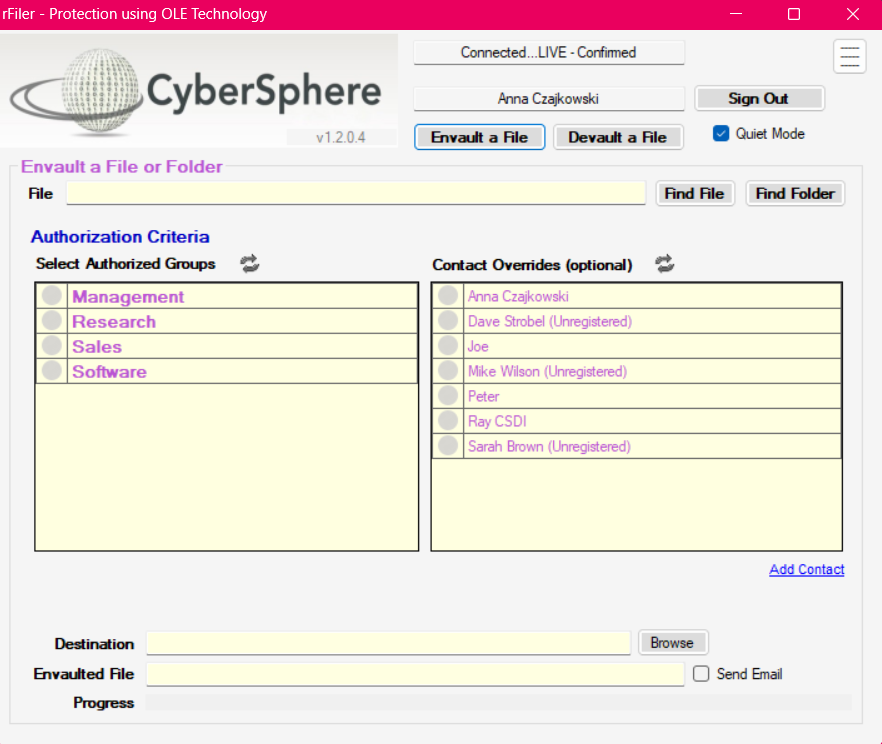
Cyber Sphere’s rFiler is a cloud application implementing the patented AutoSafe protocol. A server-side application manages access control and authentication while a client-side application performs file and folder encryption. An integrated email client enables data protection and transmission within the application.
User-defined participant groups and approved individuals ensure controlled distribution of sensitive information. Attempts by unauthorized users to open an envaulted package will fail and are detected and reported.
Features and Capabilities:
- Customizable group and user administration system: Create and manage secure user communities. Controls distribution as participants enter/leave groups. Scales from small work groups to global organizations.
- Simplified key management: Cost effective, easier to use and implement.
- Highly automated: Drives broader adaptation and utilization of encryption, better security at a much lower cost. Tracks any file, wherever it is received and sent.
- Provides comprehensive content control: Policy or message originator can redact any file/message, set document time limits for use.
- End users only need their own password. Management of second key and other processes are fully automated.
- Provides security beyond encryption: Protect / Detect / React.
- Protect: encrypt data and folders.
- Detect: report and log failed authentications.
- React: CASS can be pre-programmed with notification and reaction rules.
Download rFiler here: rFiler Install
Download rFiler User’s Guide here: rFiler User’s Guide